Install and Configure CSF ConfigServer Firewall
About CSF Firewall
ConfigServer Security and Firewall, also known as CSF, is an opensource software firewall application. It is working based on iptables. Firewall configuration script created to provide better security for your server while giving you an easy to use, advanced interface for managing your firewall settings. CSF configures your server’s firewall to lock down public access to services and only allow certain connections, such as logging in to FTP, checking your email, or loading your websites.
Features
ConfigServer Firewall CSF Provides:
- Straight-forward SPI iptables firewall script ;
- Daemon process checking ;
- login authentication failures check (ssh, mail server, ftp, webmin, virtualmin & cpanel) ;
- SSH & SU login notification ;
- Alert for spam mail scripts ;
- Suspicious process reporting ;
- Excessive user processes reporting ;
- Suspicious file reporting ;
- BOGON packet protection ;
- Port Scan tracking and blocking ;
- Permanent and Temporary IP blocking ;
- IPv6 Support with ip6tables ;
- Permanent and Temporary IP allow ;
- SYN Flood protection ;
- IDS (Intrusion Detection System) ;
- Connection Tracking and blocking
- Typical DoS and flood protection and blocking
- Distributed attacks blocking
- Suhosin failures
- Mod_security failures (v1 and v2)
- And more
Install ConfigServer Firewall
In this article, we are going to explain about ConfigServer Security & Firewall (CSF) installation and configuration in Linux. I tested this in my Centos 7 server, but this installation procedure is common for all the Linux distribution.
Make sure you have installed the following perl modules. These modules are required for Statistical Graphs available from the csf UI. It is dependent on graphical libraries being installed for your OS (e.g. libgd, libpng, etc.) The Perl module itself can be installed as shown below.
On RedHat/CentOS/:
yum install perl-GDGraph perl-libwww-perl
On Debian/Ubuntu:
sudo apt-get install libgd-graph-perl libwww-perl
Now, download the latest CSF from the official download page.
cd /opt
sudo wget https://download.configserver.com/csf.tgz
Extract csf.tgz file using command:
sudo tar -zxvf csf.tgz
A word of caution: You should not run any other iptables firewall configuration script. For example, if you previously used APF(Advanced Policy Firewall)+BFD(Brute Force Detection) you can remove the combination (which you will need to do if you have them installed otherwise they will conflict):
Go to csf directory,
cd csf/
… and run the following command to APF and BFD:
sudo sh remove_apf_bfd.sh
Sample output:
Removing apf and/or bfd…
remove_apf_bfd.sh: 5: remove_apf_bfd.sh: apf: not found remove_apf_bfd.sh: 11: remove_apf_bfd.sh: /sbin/chkconfig: not found remove_apf_bfd.sh: 12: remove_apf_bfd.sh: /sbin/chkconfig: not found
As you see in the above output, I don’t have APF & BFD in my system.
Now, let us go further and install CSF using command:
sudo ./install.sh
Sample output:
Selecting installer... Running csf generic installer Installing generic csf and lfd Check we're running as root Checking Perl modules...mode of ‘os.pl’ changed from 0755 (rwxr-xr-x) to 0700 (rwx------) Configuration modified for Debian/Ubuntu/Gentoo settings /etc/csf/csf.conf ok [....] Don't forget to: 1. Configure the following options in the csf configuration to suite your server: TCP_*, UDP_* 2. Restart csf and lfd 3. Set TESTING to 0 once you're happy with the firewall, lfd will not run until you do so ‘lfd.sh’ -> ‘/etc/init.d/lfd’ ‘csf.sh’ -> ‘/etc/init.d/csf’ mode of ‘/etc/init.d/lfd’ retained as 0755 (rwxr-xr-x) mode of ‘/etc/init.d/csf’ retained as 0755 (rwxr-xr-x) Removing any system startup links for /etc/init.d/lfd ... Removing any system startup links for /etc/init.d/csf ... Adding system startup for /etc/init.d/lfd ... /etc/rc0.d/K20lfd -> ../init.d/lfd /etc/rc1.d/K20lfd -> ../init.d/lfd /etc/rc6.d/K20lfd -> ../init.d/lfd /etc/rc2.d/S80lfd -> ../init.d/lfd /etc/rc3.d/S80lfd -> ../init.d/lfd /etc/rc4.d/S80lfd -> ../init.d/lfd /etc/rc5.d/S80lfd -> ../init.d/lfd Adding system startup for /etc/init.d/csf ... /etc/rc0.d/K80csf -> ../init.d/csf /etc/rc1.d/K80csf -> ../init.d/csf /etc/rc6.d/K80csf -> ../init.d/csf /etc/rc2.d/S20csf -> ../init.d/csf /etc/rc3.d/S20csf -> ../init.d/csf /etc/rc4.d/S20csf -> ../init.d/csf /etc/rc5.d/S20csf -> ../init.d/csf ‘/etc/csf/csfwebmin.tgz’ -> ‘/usr/local/csf/csfwebmin.tgz’ <strong>Installation Completed</strong>
After installing CSF, you can safely remove the zip file and csf directory using command:
cd /opt/
sudo rm -Rf csf/ csf.tgz
Next, test whether you have the required iptables modules:
sudo perl /usr/local/csf/bin/csftest.pl
Sample output:
Testing ip_tables/iptable_filter...OK Testing ipt_LOG...OK Testing ipt_multiport/xt_multiport...OK Testing ipt_REJECT...OK Testing ipt_state/xt_state...OK Testing ipt_limit/xt_limit...OK Testing ipt_recent...OK Testing xt_connlimit...OK Testing ipt_owner/xt_owner...OK Testing iptable_nat/ipt_REDIRECT...OK Testing iptable_nat/ipt_DNAT...OK <strong>RESULT: csf should function on this server</strong>
Cool. CSF should work in our server.
Configure CSF
Now, you should configure the TCP_IN, TCP_OUT, UDP_IN and UDP_OUT options in the csf configuration to suite your server.
To do that, edit.
sudo vi /etc/csf/csf.conf
Make the following changes:
[...] # Allow incoming TCP ports TCP_IN = "20,21,22,25,53,80,110,143,443,465,587,993,995" # Allow outgoing TCP ports TCP_OUT = "20,21,22,25,53,80,110,113,443,587,993,995" # Allow incoming UDP ports UDP_IN = "20,21,53" # Allow outgoing UDP ports # To allow outgoing traceroute add 33434:33523 to this list UDP_OUT = "20,21,53,113,123" [...]
Go through the configuration file completely and make the changes as per your requirement. Once you made all changes, enable CSF, by changing the line TESTING=”1″ to TESTING=”0″ in the csf.conf file.
TESTING = "0"
Save and close the file.
Now, start CSF service as shown below.
chkconfig csf on
sudo service csf start
Note: You don’t have to run “chkcconfig” command in Debian/Ubuntu.
Sample output:
Starting csf:Flushing chain `INPUT' Flushing chain `FORWARD' Flushing chain `OUTPUT' Flushing chain `PREROUTING' Flushing chain `INPUT' Flushing chain `OUTPUT' Flushing chain `POSTROUTING' Flushing chain `INPUT' Flushing chain `FORWARD' Flushing chain `OUTPUT' Flushing chain `PREROUTING' Flushing chain `INPUT' Flushing chain `OUTPUT' Flushing chain `POSTROUTING' csf: FASTSTART loading DROP no logging (IPv4) csf: FASTSTART loading DROP no logging (IPv6) [...] ACCEPT all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 ctstate RELATED,ESTABLISHED ACCEPT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 ctstate RELATED,ESTABLISHED ACCEPT all opt in !lo out * ::/0 -> ::/0 ctstate RELATED,ESTABLISHED ACCEPT all opt in * out !lo ::/0 -> ::/0 ctstate RELATED,ESTABLISHED csf: FASTSTART loading TCP_IN (IPv4) csf: FASTSTART loading TCP6_IN (IPv6) csf: FASTSTART loading TCP_OUT (IPv4) csf: FASTSTART loading TCP6_OUT (IPv6) csf: FASTSTART loading UDP_IN (IPv4) csf: FASTSTART loading UDP6_IN (IPv6) csf: FASTSTART loading UDP_OUT (IPv4) csf: FASTSTART loading UDP6_OUT (IPv6) ACCEPT icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 icmptype 8 limit: avg 1/sec burst 5 ACCEPT icmp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 icmptype 0 ACCEPT icmp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 icmptype 8 ACCEPT icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 icmptype 0 limit: avg 1/sec burst 5 ACCEPT icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 icmptype 11 ACCEPT icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 icmptype 3 ACCEPT icmp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 icmptype 11 ACCEPT icmp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 icmptype 3 ACCEPT icmpv6 opt in !lo out * ::/0 -> ::/0 ACCEPT icmpv6 opt in * out !lo ::/0 -> ::/0 ACCEPT all opt -- in lo out * 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT all opt -- in * out lo 0.0.0.0/0 -> 0.0.0.0/0 LOGDROPOUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 LOGDROPIN all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT all opt in lo out * ::/0 -> ::/0 ACCEPT all opt in * out lo ::/0 -> ::/0 LOGDROPOUT all opt in * out !lo ::/0 -> ::/0 LOGDROPIN all opt in !lo out * ::/0 -> ::/0 csf: FASTSTART loading DNS (IPv4) csf: FASTSTART loading DNS (IPv6) LOCALOUTPUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 LOCALINPUT all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 LOCALOUTPUT all opt in * out !lo ::/0 -> ::/0 LOCALINPUT all opt in !lo out * ::/0 -> ::/0 <strong> Done</strong>
CSF Configuration has been done…!!
Next, we will discuss CSF configuration files and it’s usage.
CSF Configuration Files
You can view the csf command line options by using either:
man csf
Or
sudo csf -h
These options allow you to easily and quickly control and view csf.
All the configuration files for csf are in /etc/csf and include:
- csf.conf: The main configuration file, it has helpful comments explaining what each option does ;
- csf.allow: A list of IP’s and CIDR addresses that should always be allowed through the firewall ;
- csf.deny: A list of IP’s and CIDR addresses that should never be allowed through the firewall ;
- csf.ignore: A list of IP’s and CIDR addresses that lfd should ignore and not not block if detected ;
- csf.*ignore: Various ignore files that list files, users, IP’s that lfd should ignore. See each file for their specific purpose and tax.
You should restart csf service if you made any changes in the configuration files.
To restart csf service, run:
sudo service csf restart
CSF Usage
Sample list of CSF Commands:
1. How to allow / whitelist an IP address?
<span lang="en">sudo csf -a 192.168.1.2</span>
This will add IP address 192.168.1.2 in /etc/csf/csf.allow.
Restart the firewall after whitelisting the IP address.
2. How to remove a blocked IP address without adding to whitelist?
<span lang="en">sudo csf -dr 192.168.1.5</span>
This will remove the IP address 192.168.1.5 from deny list
3. How to block an IP address?
<span lang="en">sudo csf -d 192.168.1.2 </span>
This will add IP address 192.168.1.2 in /etc/csf/csf.deny.
4. How to check whether an IP is blocked by CSF?
<span lang="en">sudo csf -g 192.168.1.2</span>
The above command will show whether IP is blocked by CSF.
5. How to disable csf and lfd completely?
<span lang="en">sudo csf -x</span>
6. How to enable CSF firewall?
<span lang="en">sudo csf -e</span>
7. How to restart CSF firewall?
<span lang="en">sudo csf -r</span>
8. How to Flush CSF firewall?
<span lang="en">sudo csf -f</span>
9. How to remove an IP from csf allow list?
<span lang="en">sudo csf -ar 192.168.1.2</span>
This will remove IP address from /etc/csf/csf.allow.
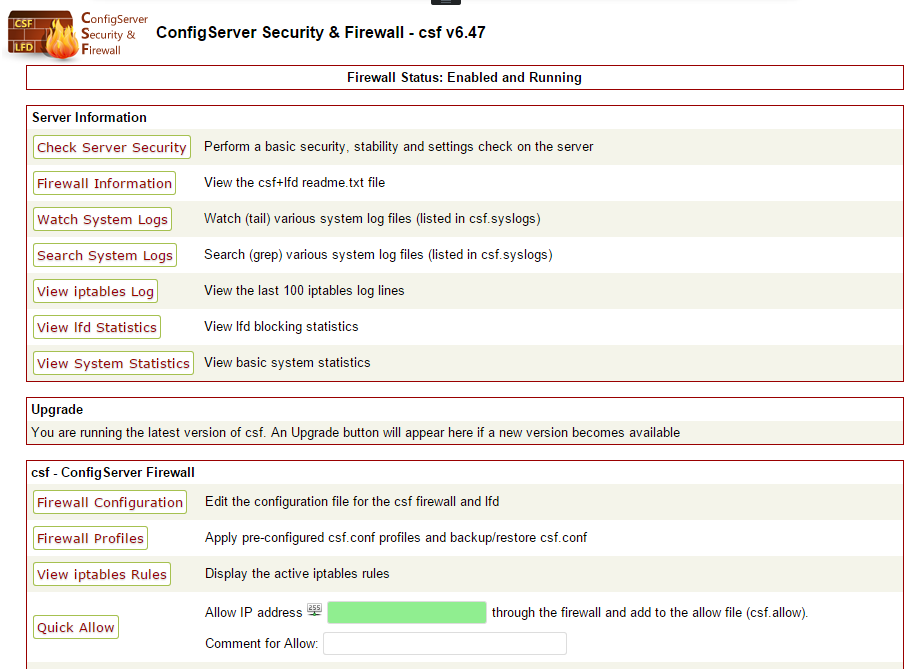
CSF GUI
In case you don’t like console, or you don’t have any experience with it, CSF also has a beautiful GUI for cPanel, DirectAdmin and Webmin.
You can install it easily, in /etc/csf/ there are instructions for all of these panels. Enjoy.
The post Install and Configure CSF ConfigServer Firewall appeared first on NixPal.
Discover more from Ubuntu-Server.com
Subscribe to get the latest posts sent to your email.


 csf
csf
